Clear the Log Jam
Become the most secure solution in your market
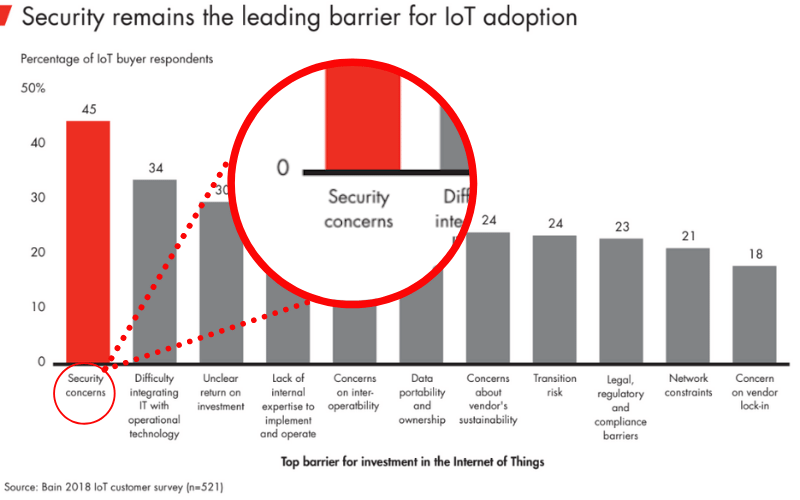
Security is the primary obstacle for IIOT
Period.
The SECURITY Log Jam
What’s holding you back?
Securing the IIOT is no small task. If you’re not there, well, you’re not alone!
Countless surveys and studies all come to the same conclusion – SECURITY is the primary blocker to bringing new IIOT products to market.

Are your products safe?
Most applications have not adequately (if at all) addressed Cyber Security. This is especially true for IIOT applications.
Does your company have the expertise to know?
Security domain knowledge is in short supply and expensive to recruit. Best practice dictates security cross-cuts the entire architecture and must go in to the design – first. Your engineers are experts in your niche, not likely closely following Cyber Security technology. That’s ok, it’s what we do!
ION’s solution works under and along side your existing application. It offers extension points for those wishing close integration, but that’s not required to gain industry standard protections with our solution.
Are you protecting your customers?
Your customers want (and need) to know you care about security, and most want to see evidence based assurance of security.
Has your company done their due diligence? Do you have ready answer for questions of cyber security preparedness? Enhancing your product to produce actual, evidence based assurance of security measures is a powerful marketing component. Trust our product so your customers will trust you.


And what about compliance?
Compliance? Isn’t that only for medical and financial applications (HIPPA, SOX, etc.)? Nope, those days are gone! It’s everyone’s concern in the 21st century.
Just think what a global technical tsunami GDPR brought, and that’s only the beginning.
Will you be ready when the GDPR equivalent requirements for IIOT security arrives? They’re here now.
Be ahead of your competition with a compliance ready product.
Break your product for security?
After an embarrassing public breach, management often demands an explanation and a promise it will never happen again.
What they often don’t understand is that adding security to an insecure implementation may not be trivial. And often, the surgery kills the patient.
Securing an existing, legacy systems usually forces radical (and costly) redesign, reimplementation, and retest.
What’s unique about ION Security’s approach is that our solution does not invade your solution or disrupt it.
It buoys it.
https://warrenrobbins.com/wp-content/uploads/2019/06/Tower-18684.mp4
Meet Your Solution
Run your software on our hardware – effortlessly
Built for Anything
Compact fanless design with wide operating temperature range
Instant Security
Up and running in minutes thanks to pre-installed system images
Sensible Pricing
Industrial capabilities at a reasonable cost
It Just Works
No need to re-design, re-engineer, or re-anything